Delivering MSPs/MSSPs
a fully-managed
SOC-as-a-Service
in the cloud.
BETTER SECURITY. LESS STRESS.
More than just technology.
The Right People.
The Right Solution.
Comprehensive and Cost-effective.
XeneX combines a highly flexible total solution with deeply integrated security tools and the peace-of-mind provided by 24/7 availability of world-class security experts.
SOC-As-A-Service
Security is evolving. Stay ahead of the curve.
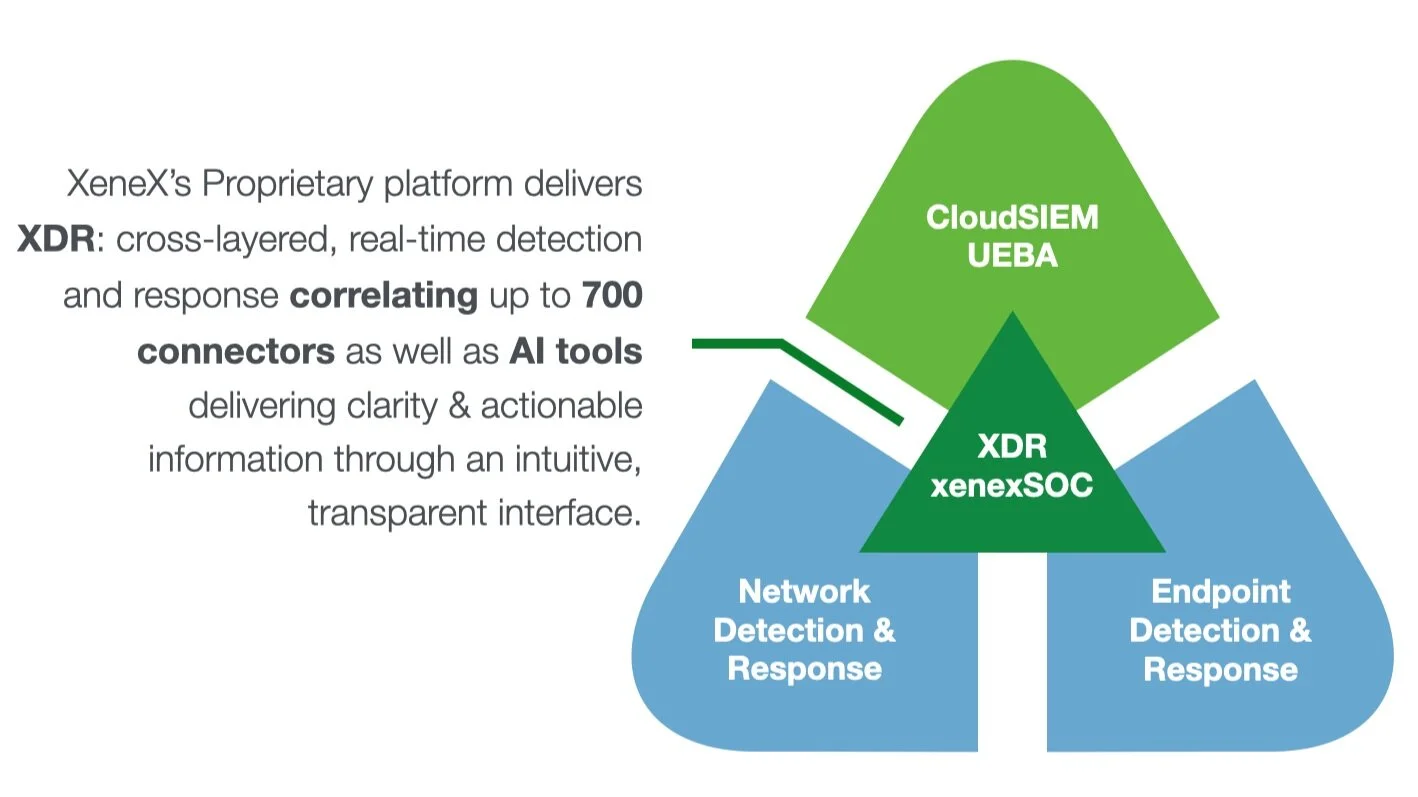
Gartner’s SOC Visibility Triad is a multi-component approach to network-centric threat detection & response. XeneX takes this one step further with its innovative SOC-as-a-Service solution that evolves from “data and dashboards” towards “clarity and correlation.”
Let’s talk.
XeneX eliminates the challenge of deploying and operating enterprise-class security by reducing your costs, risk, resource usage, time-to-market, and administrative expenses. More security, less stress. What’s not to like?
Awards & Accolades
Meet some of our partners.
Cyvent
Meet Yuda Saydun, founder and president of CyVent, where he leads the strategic direction and oversees the selection and delivery of cutting-edge, AI-driven cybersecurity products and services that protect some of the world’s most sensitive operations.
David with System Operations Strategies
Plurilock
Meet Stephen Boughton, Community Manager with Plurilock, a XeneX partner. Plurilock delivers a real-time cybersecurity solution that uses artificial intelligence to identify, prevent, and eliminate insider threats, securing the enterprise and ensuring compliance.
Byteworks
Meet James Willard, Founder of Byteworks. Byteworks is an engineering and consulting firm with broad experience in enterprise modernization, managed services, collaboration, and cybersecurity.
Osi Vision
Meet David Cartwright, Executive Director and Head of Cybersecurity with Osi Vision. Osi Vision has extensive experience supporting federal agencies and private clients with a range of technology and logistics solutions.
The latest on cybersecurity and special live events from XeneX.
Be the first for special events and updates from inside XeneX. Sign up now (spam-free zone) and keep in touch.

“XeneX technology offers a broader and deeper security operations capability than the half a dozen other companies we reviewed.”
— Kevin McDonald, COO/CISO Alvaka Networks (35+ years in business)